
SERIOUS ABOUT BUILDING IN WEB3?
If you're working on something real — let's talk.
Published On Oct 10, 2025
Updated On Oct 10, 2025

In the first five months of 2025, blockchain exploits claimed more than $2.1 billion. At the same time, crypto hack losses fell 37 percent in Q3 2025, with code exploits declining by 71 percent.
That divergence suggests code-level vulnerabilities are receding while operational and protocol-level risks are rising.
Trust today depends less on bug-free code and more on how disputes are resolved, how data is stored, and how control is distributed.
Early Web3 relied on audits, multisigs, and bug bounties as reactive defences against errors after they surfaced.
Modern systems bake security into design: proof systems, restaking markets, and data availability layers now form the backbone of trust.
Each carries trade-offs: speed vs decentralization, scalability vs cost, shared security vs sovereignty.
Security protocols should be treated as infrastructure, not add-ons.
For readers seeking a broader view beyond security architecture - including protocol performance, scalability, and ecosystem adoption metrics - explore our detailed Top Protocols 2025 Guide.
This blog unpacks how leading blockchain networks have redefined security as architecture, analyzing how economic, cryptographic, and operational guarantees combine to form measurable, composable trust systems.
Security is shifting from reactive protection to proactive design.
Instead of relying on audits or bug bounties, leading protocols are embedding trust directly into their validation, proof, and data layers.
Here’s how the global security landscape looks today:
Protocol-level security in 2025 is quantitative and layered, measured through staked capital, proof of efficiency, and verifiable data integrity rather than traditional audits.
Together, these developments signal a maturing security landscape where resilience is no longer abstract but measurable.
As blockchain networks evolve into complex, multi-layered ecosystems, evaluating their security now requires clear, quantifiable benchmarks rather than subjective assessments.
As blockchain ecosystems scale, comparing their security requires objective, quantifiable parameters, not subjective claims.
These dimensions are consistent across leading research frameworks and provide a measurable way to evaluate how economic, cryptographic, and operational security interact in modern blockchains.
These four metrics are measurable across ecosystems and describe the economic, cryptographic, and operational layers that together form blockchain security.
The evaluation is grounded in publicly verifiable data from sources such as L2BEAT, DefiLlama, and Beaconcha.in, complemented by insights from official documentation and audit reports published through October 2025.
The protocols below represent the leading examples of how blockchain networks in 2025 secure trust across distinct architectural layers.Each category highlights a different approach to balancing decentralization, performance, and assurance.
To make this comparison more structured, we’ve grouped them into categories based on their primary security function, from settlement and consensus integrity to shared restaking, data availability, cryptographic verification, and optimistic proof models.
Protocols anchoring global settlement and validator-based consensus integrity.
This category represents the foundational layers where economic capital and validator consensus safeguard the entire Web3 ecosystem’s trust base.
Networks extending validator capital across multiple ecosystems to create reusable trust markets.
These protocols redefine security as a shared resource, enabling new chains and services to borrow economic trust instead of bootstrapping it from scratch.
Systems ensuring verifiable data access and modular availability for rollups.
This category focuses on how blockchains store, sample, and verify transaction data, ensuring scalability without sacrificing transparency.
Protocols proving computational correctness through zero-knowledge proof mechanisms.
These systems use advanced cryptography to mathematically guarantee that every computation is correct, eliminating the need for trust in intermediaries.
Rollups balancing cost and assurance through fraud-proof and challenge-based finality models.
Each of these categories reflects a different security philosophy from Ethereum’s capital-backed settlement to Celestia’s modular data availability and Starknet’s zk-verified execution.
Together, they define how blockchain security in 2025 has evolved from code protection to architectural assurance, where trust is engineered through layers, not audits.
The following dataset provides a detailed snapshot of these ten protocols, illustrating how each translates its design principles into measurable, verifiable security outcomes.
The following snapshot compiles verified data from L2BEAT, Beaconcha.in, and DefiLlama(Oct 2025), highlighting how the top 10 protocols distribute trust across these security dimensions.
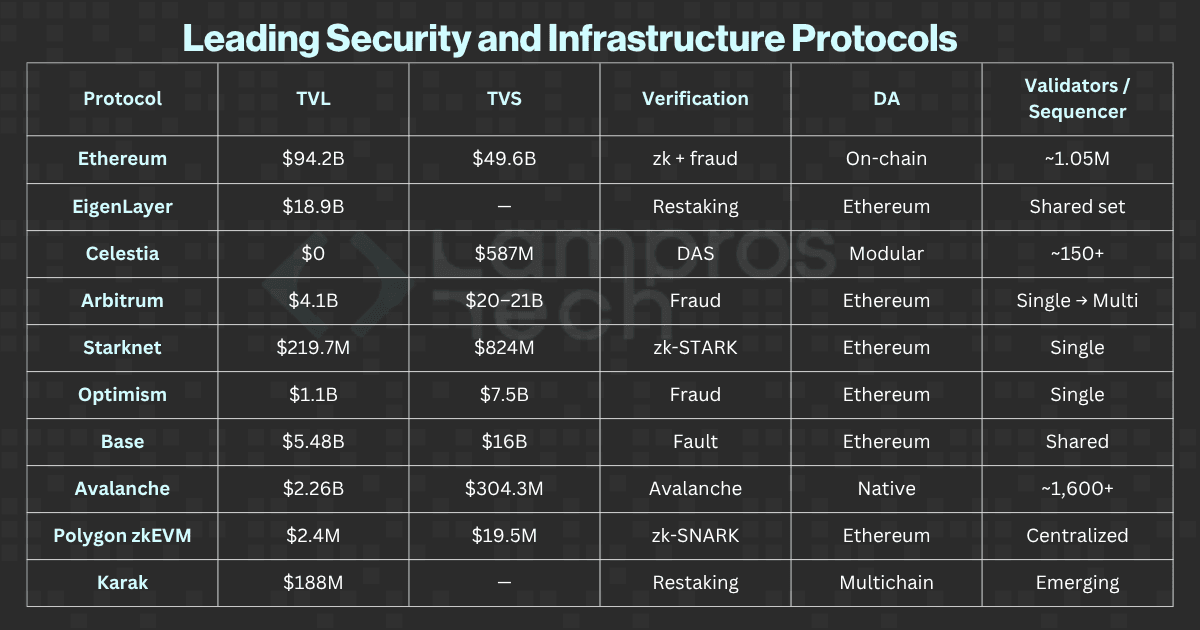
In the next section, we translate this landscape into a structured model, the Security Stack, where economic, cryptographic, and operational layers work in tandem to create verifiable trust for modular blockchains.
Every blockchain composes security differently.
While Ethereum anchors economic trust, newer systems extend, modularize, or automate it through restaking, proof markets, and verifiable execution.
Here’s how ten leading protocols structure their stack across economic, cryptographic, and operational layers in 2025.
Takeaway: Ethereum remains the most secure economic root slow but incorruptible, defining the benchmark for validator dispersion and settlement assurance.
Takeaway: Avalanche shows that sovereignty can scale fast, customizable, and secure, but economically isolated from shared validator pools.
Takeaway: EigenLayer transforms staking into programmable infrastructure, scalable but interconnected, requiring careful risk segmentation.
Takeaway: Karak pushes restaking toward interoperability, expanding reach but introducing validator coordination complexity.
Category Insight: Shared security enables faster ecosystem growth but centralizes validator exposure, making slashing, delegation, and monitoring critical design levers.
Takeaway: Celestia proves that DA is the new consensus enabling modular rollups with scalable, verifiable data layers.
Category Insight: Data availability is now as critical as consensus. Celestia leads this shift by making DA a standalone, cryptographically verifiable service.
Takeaway: Starknet demonstrates that zk proofs can deliver deterministic trust at scale, though at a higher computational cost.
Takeaway: Polygon zkEVM bridges enterprise adoption with zk-level assurance, combining Ethereum-grade security with modular deployment tools.
Category Insight: zk-proofs are now production-ready. zk-STARKs prioritize transparency and scalability, while zk-SNARKs optimize for proof efficiency and enterprise integration.
Takeaway: Arbitrum balances scalability with conditional trust finality delayed by design for verifiability.
Takeaway: Optimism turns fault-proof into a shared standard, enabling modular rollups and enterprise-grade deployment at scale.
Takeaway: Base demonstrates that optimistic frameworks can achieve institutional trust through transparency and shared validation.
Category Insight: Optimistic systems remain cost-efficient and developer-friendly; their success now hinges on decentralizing sequencers and tightening fraud-proof cycles.
Each protocol represents a distinct security philosophy:
Together, these systems mark the transition of blockchain security from a defensive measure to an engineered architecture measurable, layered, and composable.
Across these ecosystems, one theme stands out: security is no longer siloed.
Economic guarantees, cryptographic proofs, and operational reliability now interlock as modular layers of trust.
Each protocol emphasizes a different layer
Together, they define the blueprint of blockchain security in 2025, composable, verifiable, and measurable by design.
Next, we explore the key trade-offs shaping secure blockchain design — and how to build resilient, verifiable protocols in 2025.
Building a secure protocol in 2025 isn’t about audits or compliance checklists; it’s about engineering resilience across architecture, governance, and people. Attackers now exploit not just smart contracts, but validator setups, upgrade pipelines, and even the humans behind multisigs.
To stay ahead, teams must:
But these are just the fundamentals. In our detailed guide, we break down the entire blueprint from AI-based defense systems to governance hardening and validator security frameworks that leading protocols now rely on.
For a deeper technical guide on operationalizing these principles, explore Web3 Web3 Security 2025: AI Tools and Best Practices blueprint for next-generation protocol security.
In 2025, security isn’t a checklist; it’s the foundation of credibility.
What to Look for When Evaluating a Protocol -
The most trusted protocols don’t just deploy safer code; they embed integrity into their design, aligning economic incentives, cryptographic proofs, and operational guarantees into one verifiable system.
Every architectural choice now carries a security consequence.
Together, these principles define a new paradigm, Security-as-Architecture, where resilience, verifiability, and modular design converge to form the backbone of blockchain trust.
The projects that will endure are those that can prove security, not claim it. Because in Web3, credibility is no longer declared; it’s demonstrated at every layer.
At Lampros Tech, we help teams design, develop, and deploy secure blockchain protocols and decentralized exchanges (DEXs) built for the realities of 2025, where transparency, composability, and verifiability define trust.
Explore our Secure DEX development Services and see how Lampros Tech integrates security, scalability, and speed into every protocol we build.
Because in the next era of Web3, trust isn’t claimed, it’s engineered.

Blockchain security in 2025 is defined by economic stake, cryptographic proofs, and operational decentralization. Instead of relying solely on audits, protocols embed trust into architecture using restaking, zk proofs, and modular data availability layers.

Restaking allows validators to reuse their staked assets across multiple networks, extending security through shared economic guarantees. Platforms like EigenLayer and Karak enable this, improving capital efficiency but introducing correlated risk.

Data availability ensures that all transaction data is accessible and verifiable by the network. Without it, nodes can’t confirm state validity, making blockchains vulnerable to hidden data or censorship. It’s now a foundational layer for modular and rollup-based architectures.

zk-rollups use cryptographic proofs for instant, verifiable finality and stronger security. Optimistic rollups rely on challenge periods and fraud proofs, offering cheaper, faster transactions but with delayed finality and trust in honest participants.

Key metrics include Total Value Locked (TVL), Total Value Secured (TVS), verification model (zk, fraud, or hybrid), data availability model, and validator decentralization, which define a protocol’s economic, cryptographic, and operational resilience.
DEX Infrastructure
Talk to our team about building intent-based, cross-chain, and MEV-safe trading systems.
Let’s Talk